Threat Hunting - Zero to Hero
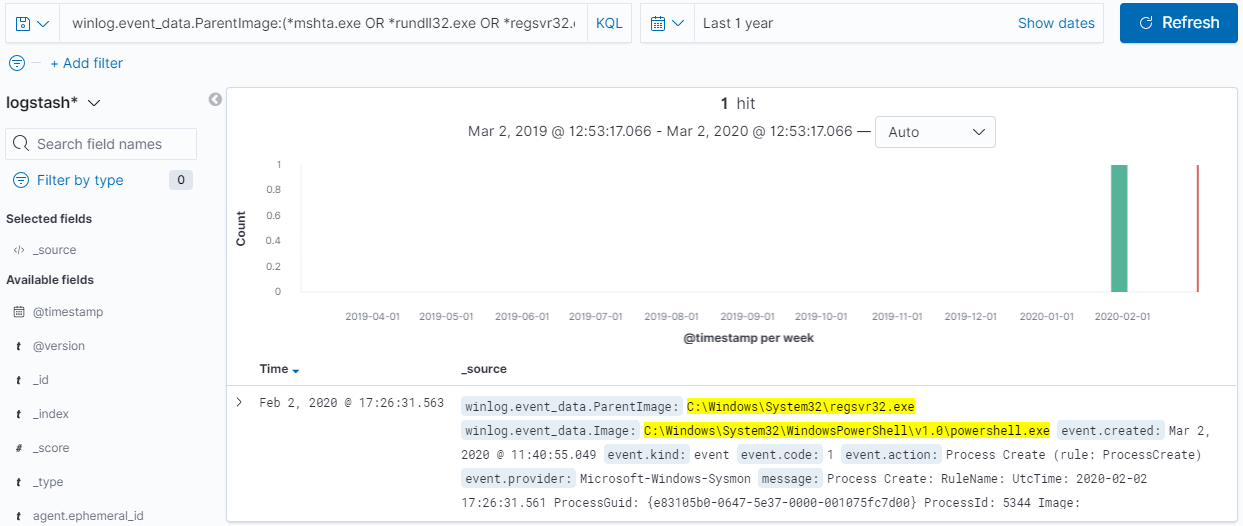
In my Securing Windows environments post, I touched upon logging and SIEM but I didn't go deeper as the post became too lengthy already. As a reference, I stated the following: "... All of the things described up to this point, aim to reduce the attack surface (reducing the risk of successful compromise) and the impact should one occur ... Now, if you think about this, the Penetration testers will be running tools and scripts, which are not normally executed in your environment so that puts you a step further, because it will all be executed on a device that you own. At this point, having and analyzing logs (default Windows logs only are insufficient to trace activity) is fundamental. In fact, in 2019, there should be no excuse for not having a SIEM system, even if it is a free of charge one - ELK stack or Graylog (although it may not have every feature you wish it did)." Basics The above refers to utilizing the available logs to perform Threat Hunting. Threat hun